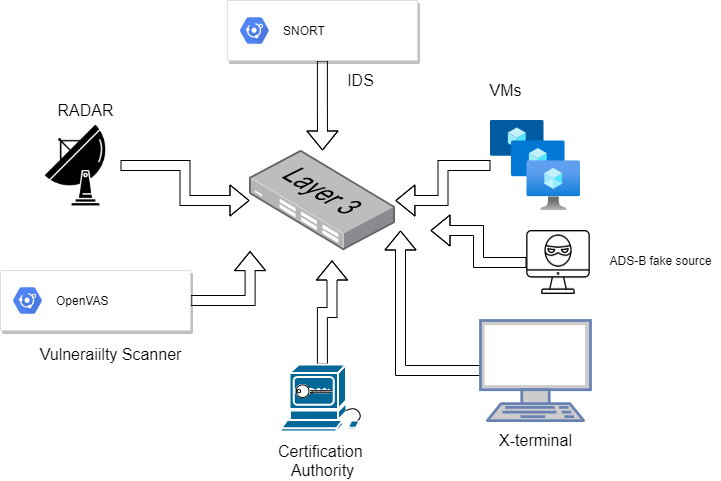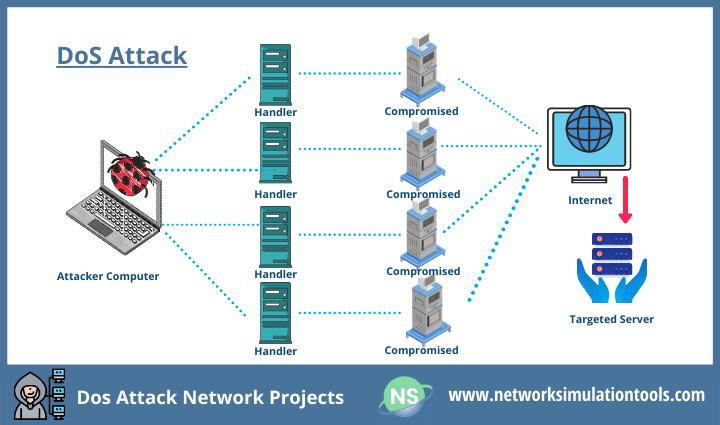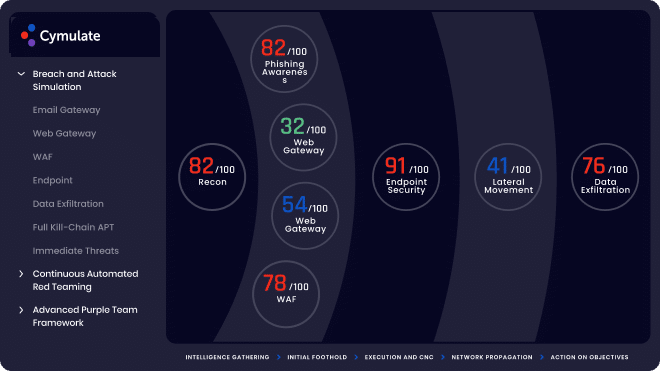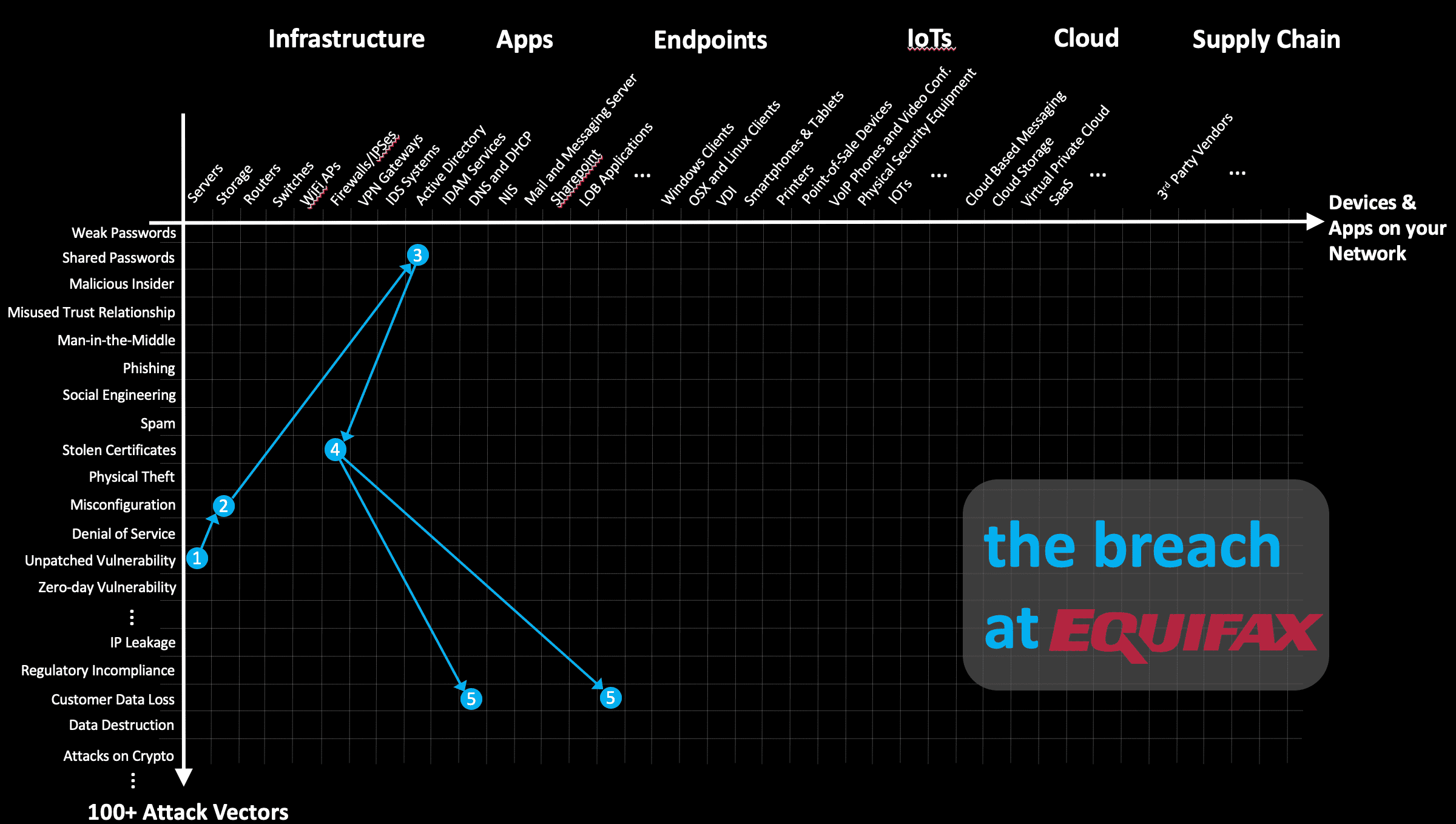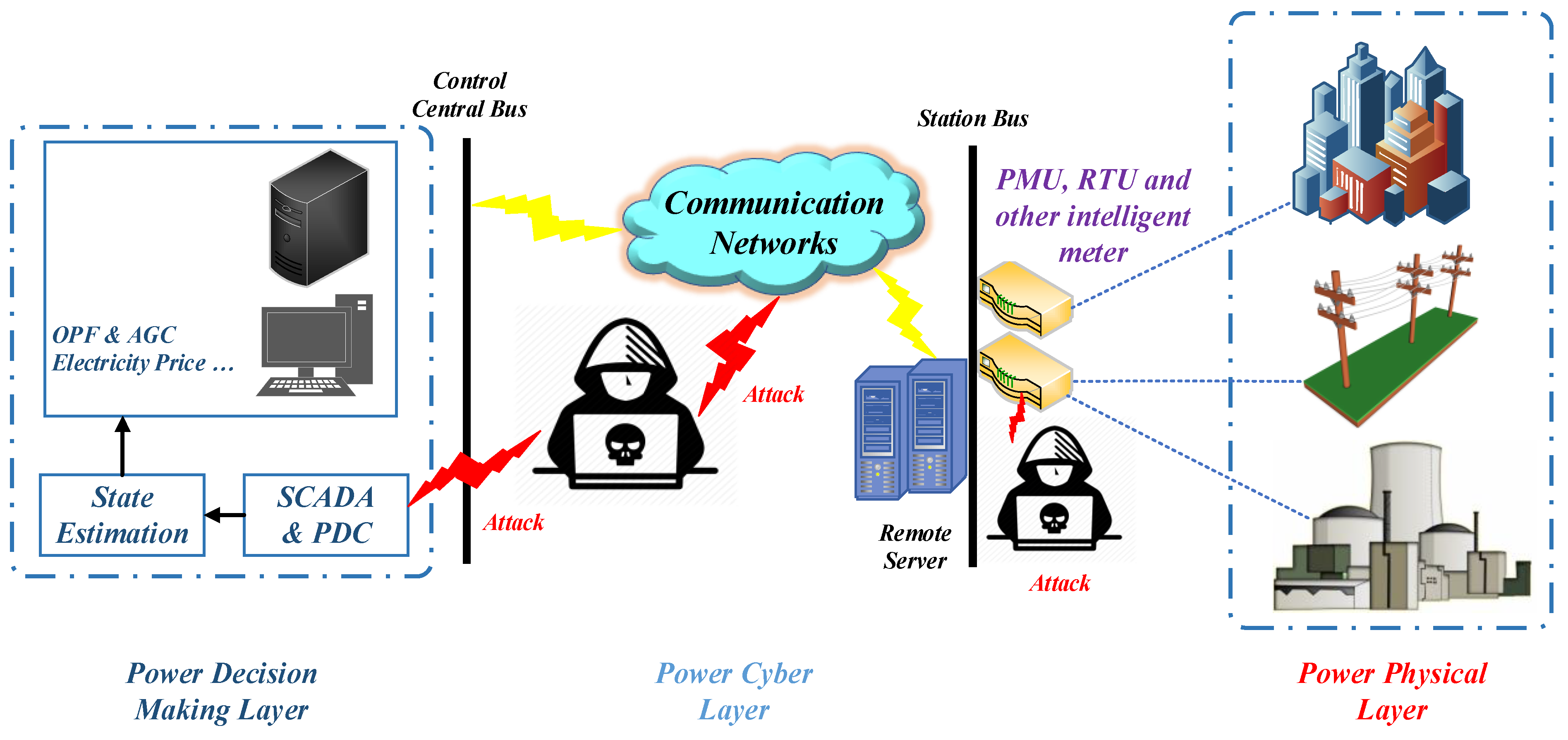
Mathematics | Free Full-Text | Deep Machine Learning Model-Based Cyber- Attacks Detection in Smart Power Systems
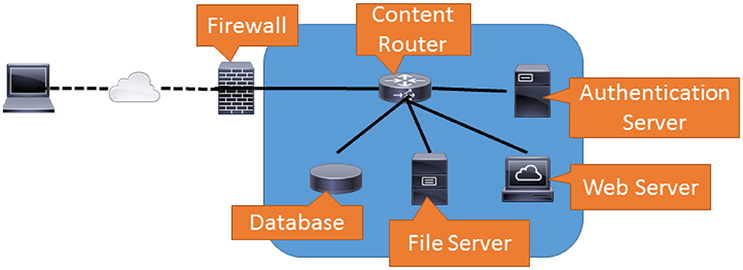
Frontiers | Simulations in Cyber-Security: A Review of Cognitive Modeling of Network Attackers, Defenders, and Users

Cyber threat assessment via attack scenario simulation using an integrated adversary and network modeling approach | The Society for Modeling & Simulation International